Oracle Business Intelligence (BI) is designed to provide open, complete and integrated solution including dashboards, ad hoc query and analysis, score cards and enterprises.
Some of the aspects offered include an expansive spectrum of embedded search, visualization options, mobile access and collaborative applications along with Microsoft Office integration. Users are afforded the ability to initiate most of these actions from a dashboard environment.
Oracle Business Intelligence Foundation Suite
The Oracle BI Foundation Suite is designed to be a common enterprise information model which enables users to ensure accurate and consistent information on a continual basis at any location. In particular, Oracle Business Intelligence technology tools include:
- products for query and analysis;
- enterprise reporting; and
- highly scalable, architecturally unified technology foundation.
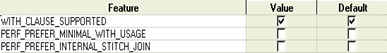
The OLAP server is designed to enable rapid modeling of security solutions which streamline forecasting, management reporting and variance analysis processing. Real-time decision solutions were developed to optimize:
1. Defined repository security. Oracle Business Intelligence provides an administration tool that may be used to create groups and users with particular and specified permissions that are defined through certain types of authentication. Once the permissions are assigned, permissions are granted to specific groups and users.
Privileges granted with exclusivity most often have precedence over group privileges. When conflict exits, privileges with least restrictions will apply.
2. Database authentication. Below is the process used for authenticating the database:
- Adjustments are made in the NQSConfig.ini file to authenticate the database.
- Security section specifies the authentication database.
- Users are created in the repository which identical to those in the database.
- Users are assigned privileges.
- Database is imported to physical repository layer using the DSN of each particular database. For example, a connection pool may incorporate a non shared logon.
- The new connection pool is used to connect to the database.
Upon connection, authentication has been effected successfully.
3. Lightweight Directory Access Protocol (LDAP) authentication. Many businesses, companies and enterprises have implemented LDAP server authentication as part of their Oracle Business Intelligence solution. One popular aspect of this is the Active Directory Service Interface (ADSI) for client projects.
The LDAP server is created in the security manager. Below is the process:
- At Action> New> LDAP Server, access the Server dialog box
- Assign parameters such as port no., host name, LDAP version (the default is 3), base DN and bind DN from the general settings.
- Define the settings in the Advanced tab by filling in aspects such as Connection Time-Out, Enable/Disable SSL and Domain Identifier.
- Create an LDAP initialization block, associated with the LDAP Server.
- Define USER as a system variable, mapped to LDAP uid.
- Alternatively, it is also possible to use the LDAP server exclusively to import group and user definitions. This scenario would be utilized if external authentication is not desired by LDAP.
4. External table authentication. The External Table Authentication is implemented by establishing a table within the database that includes columns defining aspects such as passwords, users, groups, display name, the log level, display name and security level and privileges. The table for authentication is created as follows:
- To connect to the db/table, created a new physical layer connection pool.
- Establish an initialization block with the newly defined connection pool for the table.
- Define initialization aspects such as the password, username, lognumber, and groupname from the auth_table where username = ':USER' and password = ':PASSWORD' is located).
- Define the corresponding variables (such as user, password, group, loglevel).
- Ensure that the variables order is identical to that of the initialize.
The above describes some of the processes by which the extensive Oracle Business Intelligence solutions may be utilized for an effective security strategy.

Comments
Comments not added yet!